Creating a hash file from a data file + Man-in-the-Middle attacks against keyless hashing
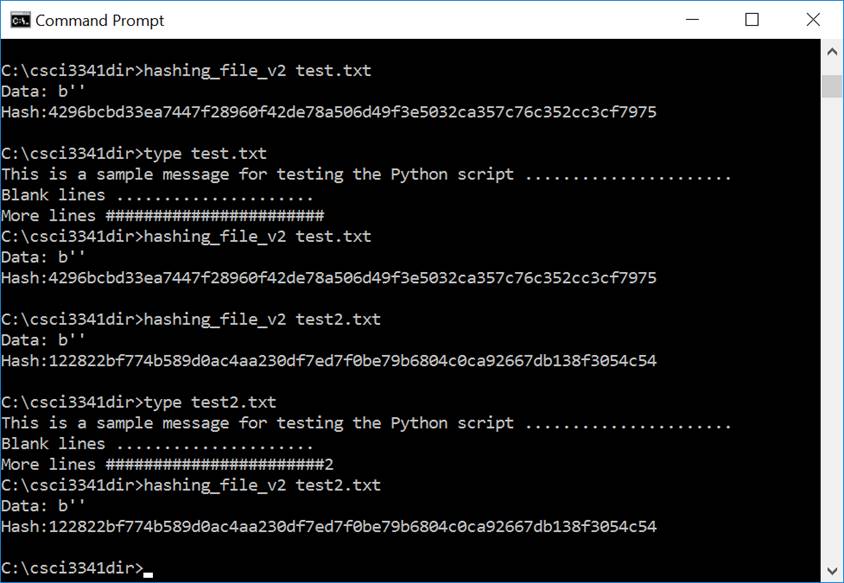
· This program, hashing_file_v2.py, reads data bytes from a file, whose name is entered by the user from the keyboard, and then generates the hash value of those data bytes on the screen. Sample screen outputs of running the script with various data files are shown in Figure 1.
Figure
1. Sample screen outputs of running hashing_file_v2.py
· EX1: (20 pts) Create two data files. Run the script using the two files as shown in Figure 1. Hand in the screen output showing the content of the data files and the generated hash values.
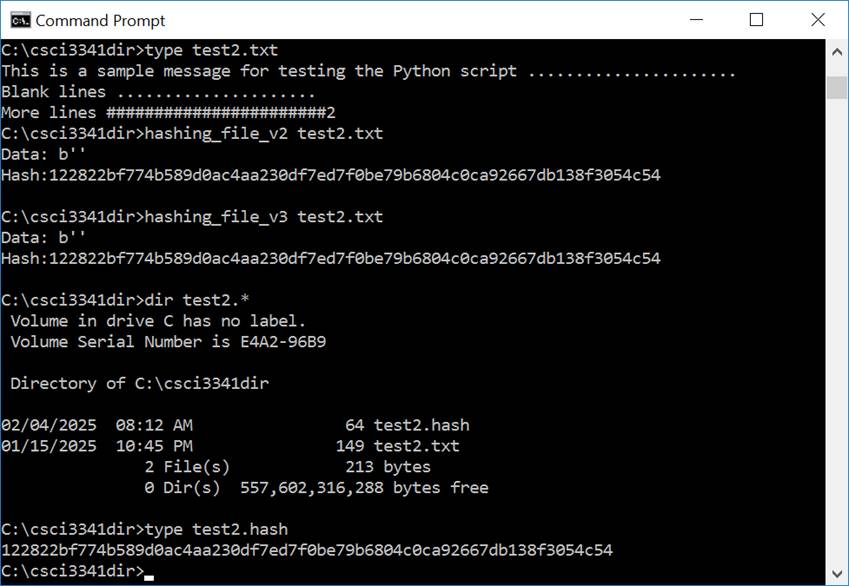
· EX2: (50 pts) Revise the script such that, in addition to displaying the generated hash value on the screen, the hash value is saved into a hash file (with the same file name but the suffix .hash). Verify the content of the hash file is the same as the hash value shown on the screen, as shown in Figure 2.
Hint: from pathlib import Path
The script in Listing 3.2 of the textbook demonstrates how to set up the suffix of the hash file.
To hand in: (a) The revised script; (b) A screen output of running the revised script, similar to Figure 2.
Figure
2. Sample screen outputs of running hashing_file_v3.py, which you will create.
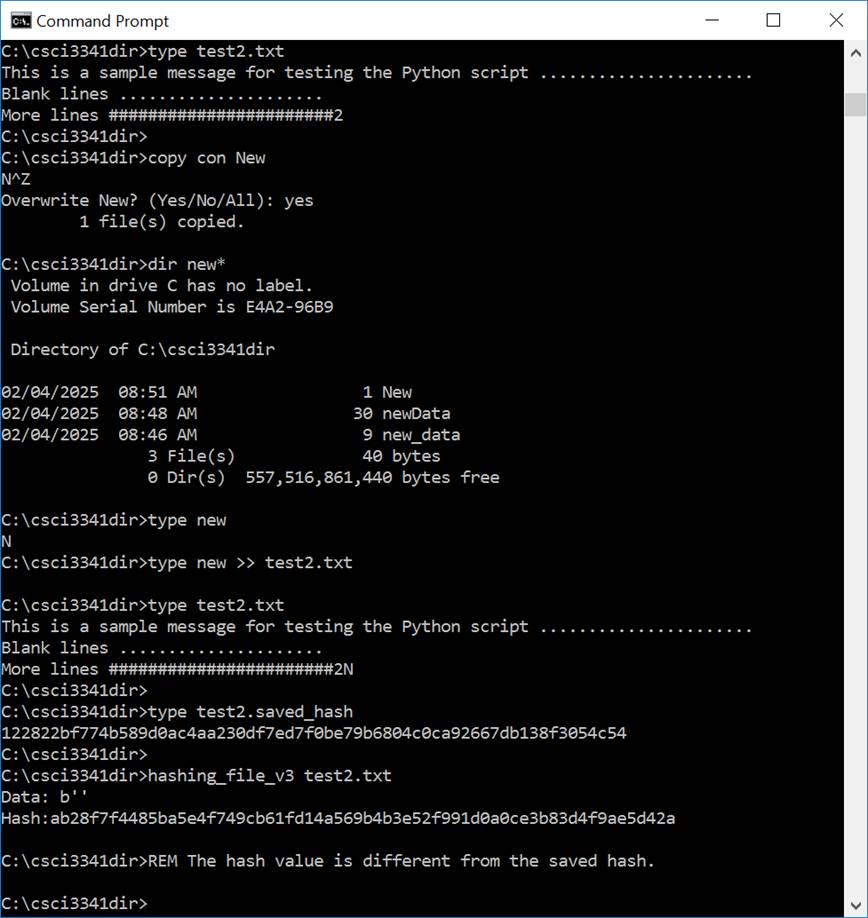
· EX3: (30 pts) Suppose the content of the hash file (i.e., test2.hash) was saved (say, in a file called test2.saved_hash using the copy command). As shown in Figure 3, when the content of test2.txt is changed (for example, by appending a single ‘N’), the generated hash value is different from the saved hash. The user of a file can therefore compare the new hash value against the saved hash value of that file to determine whether data integrity is provided (that is, whether the content of that file can be trusted or not).
To
hand in: Repeat this exercise and hand in the screen output similar to
Figure 3.
Figure
3. Sample screen outputs of running hashing_file_v3.py against a modified
test2.txt
· (Bonus) EX4: (50 pts) In a Man-in-the-Middle attack, the attacker changes the data and generates a new hash value out of the modified data. The attacker then uses the modified data and hash value to replace the original data and hash value. When the user tries to validate the integrity of the data file, he/she/it will determine that the content of that data file is correct. Therefore, a successful man-in-the-middle attack will defeat the ‘data integrity’ service, which is supposed to be provided by using hashing.
In this exercise, simulate a man-in-the-middle attack by revising your hashing_file_v3.py. The revised script will open and read an existing data file, modify its content, generate the new hash value, and then use the new hash value to overwrite the original hash file.
To
hand in: (a) The revised script; (b) A screen output of running the revised
script.