|
T. Andrew Yang
|
last updated: 10/30/2018:
Lab 5 posted 10/25/2018:
Lab 4 posted 10/16/2018:
Lab 3 posted 9/18/2018:
Lab 2 posted 8/27/2018:
first posted |
CSCI
5233 Computer Security & Cryptography
Total: 100 points
1.1. (10 pts)
Visit the class discussion group (link available in the syllabus page). Post
a message with your full name as the subject line. In your post, briefly
introduce yourself (including your full name) and one item you most desire to
learn in this class. Throughout this class, you shall regularly participate at
the discussion group to find recent announcements, reminders, and
discussions.
1.2. Java Cryptography
If you
have not done so, you may want to download the most recent Java Development Kit
from http://java.sun.com/j2se/ (for
example, JDK 6.0).
Review
information in the file ďInstallation
of JCE security provider for unlimited strength securityĒ, and become
familiar with JCE security providers and the unlimited strength Java security
policy.
Note:
The instructions given in the document have been rigorously
tested and, if followed correctly, should enable your Java environment
to run all the sample programs that come with the 'Java Security' book. If you
run into problems, double check and make sure you have
correctly completed the required steps.
Note:
Sample programs from the book are available on line at http://sce.uhcl.edu/yang/teaching/proJavaSecurityCode.html.
A zip file is available at the top of
that page for you to download all the sample programs.
After you have properly configured your Java
environment, perform the following tasks:
a. (25
pts) Test the FileEncryptor.java program
(from chapter 4 of the Garms and Somerfield book).
Add a printline statement at the beginning of the
program to print your name as part of the programís output. Run the program
using sample data of your choice.
Note: If necessary,
replace all occurrences of the cipher ĎPBEWithSHAAndTwofishí with ĎPBEWithMD5AndDESí in the source program.
To
hand in: The revised source program and the screen
output from the program
b. (Continued
from a above, 25%) Give the TA a demo
during his/her office hours before the due date.
1.3. In an online banking application, the
customer may transfer fund between the saving account and the checking account.
a.
(5 pts) Explain
what data integrity means in this context.
b.
(5 pts) Explain
what origin integrity means in this context.
c.
(5 pts) Explain
what availability means in this context.
d.
(5 pts) Explain
what confidentiality means in this context.
e.
(5 pts) Explain
what non-repudiability means in this context.
1.4. Cyber attacks: Explain what each of the following
attacks is. Cite your source(s). Note: Not all information published on the web
are correct; discern the validity of the information you use.
a.
(5 pts) Replay attacks
b.
(5 pts) Man-in-the-middle
attacks
c.
(5 pts) Keylogging
Go to
the Index
Total:
100 points
2.1.
(10 pts) Explain the differences between a replay
attack and a Man-in-the-middle
attack.
2.2.
(10 pts) Would an enciphered message be prone to replay attack? Justify your
answer. (That is, if your answer is yes, explain why; if your answer is no,
explain why not.)
2.3.
(10 pts) Would the digital signature algorithm be vulnerable to replay attacks? Justify
your answer.
2.4.
(10 pts) Explain how timestamping would be used in a protocol to mitigate replay attack.
2.5.
(15 pts) Explain what a domain name server (DNS) is, and how a DNS
server is used to support computer-to-computer communications. Cite your
source.
2.6.
(15 pts) Describe what a DNS
pollution attack is, and how it would be launched
by the hacker. Cite your source.
2.7.
(15 pts) Explain how a hacker may use a polluted DNS server to launch a
main-in-the-middle attack.
2.8.
†(15 pts) Suppose User_A has
successfully deceived User_B by making User_B trust that User_Aís public
key is User_Cís public key. That is, when User_B looks up User_Cís public
key in its public key table, User_B will find User_Aís public key instead. Explain what attacks User_A may further launch against User_B.
Give details of two types of attacks based on an incorrect public key.
Go to
the Index
Total:
100 points
3.1 Test
the FileEncryptorRSA.java program (from chapter 5 of the Garms and Somerfield book).
1)
(15 pts) Add a printline statement at the beginning of the program to
print your name as part of the programís output. Run
the program using sample data of your choice. Note: If
necessary, replace all occurrences of the cipher ĎPBEWithSHAAndTwofishí with ĎPBEWithMD5AndDESí in the source
program.
Hand in the revised
source program and the screen output from the program.
2) (continued
from above, 15%) Give the TA a demo during his office hours before
the due date.
3.2 SSL certificates
Note: When answering the questions, you must
cite the source of information you include in the answer, unless it is totally
your own. Refer to this page (http://sce.uhcl.edu/yang/citing.htm) and follow
the suitable practice in properly citing data sources. Points will be deducted for answers that do not exhibit proper
citing. Use the IEEE format for references.
Resource links:
∑ Symantec white paper, Beginnerís Guide to SSL Certificates (local
copy)
Note: Be a critical investigator! You answer
should NOT be solely based on the above white paper. Review what you learned in
class about digital certificates, and also refer to
other resources to finalize your answers.
Suppose there exists an online
company (C), and a customer (A) has visited Cís online shopping site. To earn
the customersí trust, C has a digital certificate installed on its webserver.
a.
(10
pts) Explain how Cís
certificate would be created. By whom? Draw diagrams
if necessary to enhance your explanation.
b.
(10
pts) Explain how Cís
certificate would be verified by Aís browser.
c. (10 pts) What are accomplished by the handshake process
between Aís web browser and Cís web server?
d. (15 pts) A successful handshake between
the browser and the server is followed by a
secure session. Explain which of the security services
(confidentiality, data integrity, origin integrity, availability, and
non-repudiability) are provided in a secure SSL
session. Justify your answer by explaining how each of the applicable
security services is enabled.
e. (10 pts) Suppose H has taken Cís certificate and
manually changed the subject information in
Cís certificate from C to H. Would this modification be detected by A
during the certificate verification process? Justify your answer.
f. (15 pts) Suppose a hacker has set up a rogue
web server, H, and uses Cís certificate as its own certificate, and suppose A
has visited H to do some online shopping. Explain how A would
detect that the digital certificate presented by H is not valid.
Go to
the Index
Total:
100 points
4.1 (10 pts) Using the Extended Euclidean Algorithm (EEA),
find x and y such that 35 x + 23 y
= 1.
4.2 (10
pts) Solve 17d
mod 24 = 1. What is the value of d?
4.3 (20 pts) If you had
received an email from someone called A, and Aís digital certificate was
attached to that email. Suppose Aís certificate was issued by a company called
CA, and your computer does not have CAís certificate but has another CA called CAx, which happens to be the issuer of CAís certificate.
Show how your computer would validate Aís certificate to determine
whether that certificate was a valid certificate of A.
4.4 (20 pts) Explain how a
digital certificate attached to an email may help to provide author
origin integrity (that is, the receiver of such an email can be sure
that the particular email sent from A was indeed authored by A and not anybody
else).
Hint: Devise an emailing
protocol that provides author origin integrity by using digital
certificates. Note: Cite the source of information used in your
answer, unless you are the one that have developed that protocol.
4.5 (20 pts) Explain what
additional mechanism(s) will be needed in order for the protocol you devised
above to provide sender origin integrity. Present the complete protocol.
4.6
Run the KeyAgreement application in Chapter 5 of
the Professional Java Security book. The application consists
of two Java programs (KeyAgreementClient.java and KeyAgreementServer.java).
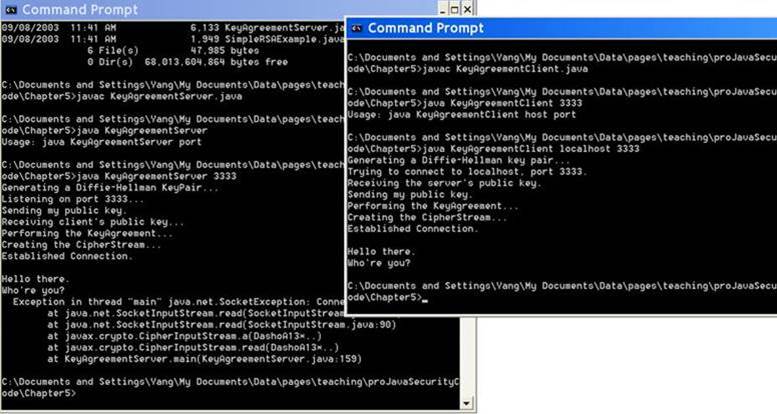
Figure 1. Demo of the
KeyAgreeement application (original)
(Bonus Project)
4.6.2 (30 pts)
Revise the KeyAgreementServer.java program,
so each time the server program receives a NewLine character sent from the client,
it will display a message like ĎLine <n> from the client: <the
mesg>Ď. See Figure 2 for a sample screen snapshot of a revised program.
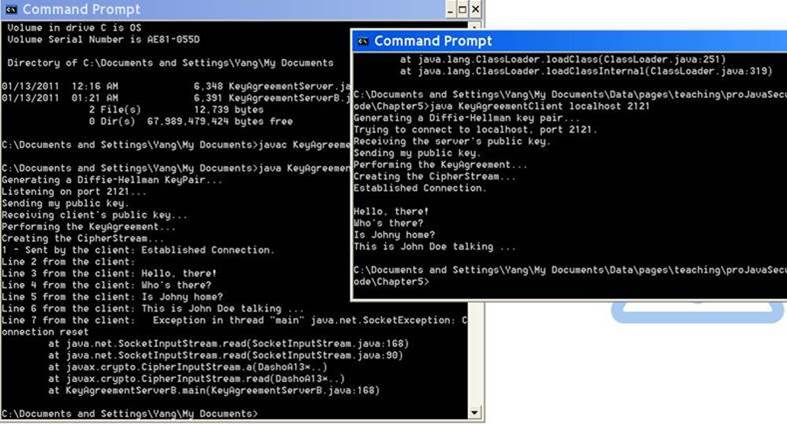
Figure 2. Demo
of the KeyAgreeement application (with revised KeyAgreementServer.java)
Go to
the Index
Total:
100 points
5.1. Suppose
a small company has grown into a much larger company, with the companyís headquarter
plus 12 branch offices across the US; each office has its own servers,
workstations, and other assets. Use this scenario as the base when answering
the following questions.
5.1.1.
(25
pts) Explain why the Kerberos protocol
would be an ideal authentication protocol when a company has expanded its company
network. Explain the benefits.
5.1.2.
(25
pts) Explain how Kerberos would be configured
in this context (when the company is expanding).
5.2. Suppose you are being
interviewed for a computer security specialist position in a major bank.
Your interviewer happens to be the director of that bankís
networking systems. Below are information provided to you by the interviewer:
All network
communications between the computer workstations/desktops used by the bankís
employees are required to authenticate each other (before sensitive data are transmitted). To enable computer-to-computer
authentication, digital signatures have been adopted.
5.2.1.
(25 pts) Explain in detail how digital signatures would be
used to enable mutual authentication
between two computers. Hint: Clearly state any prerequisites. Show the detailed
steps.
5.2.2.
(25 pts) Continued with the same scenario: Explain in detail how message
authentication codes (MAC) would be used to enable mutual authentication between two
computers. Hint: Clearly state any prerequisites. Show the detailed steps.
(Bonus)
5.2.3.
(25 pts) Continued with the same scenario: Explain in detail how digital certificates would
be used to enable mutual authentication
between two computers. Hint: Clearly state any prerequisites. Show the detailed
steps.
Go to
the Index