|
T. Andrew Yang Email: yang@uhcl.edu Web: http://cse.uhcl.edu/yang/ Tel.: (281) 283-3835 |
Last updated: 1/19/2022:
first posted |
|
||||||
|
CSCI 5233 spring 2022 Note: Note 1: The lab may be completed by an individual person or by a team of two
persons. A team can consist of no more than two
persons. Note 2: Each person in a two-person team must submit his/her own copy of the
lab. Note 3: Configure your own desktop or laptop
to implement the hands-on labs (by setting up virtual boxes and virtual hosts
on it). Note 4 (Preparation for the hands-on
labs): Go over the following
documents before starting your hands-on labs. Lab 1 Total: 100
points 1. (5 pts) Decide whether you want to work on this lab by yourself
(i.e., a one-person lab team), or partner with another person in the class
(i.e., a two-person team). Indicate your team membership for this lab.
NOTE: This task is required of each person, whether he or she is in a
one-person or a two-person team.
2. (5 pts) Visit the class discussion group in the
Blackboard. Post a message, in the forum ‘self-intro’, with your
full name as the subject line. In your post, briefly introduce yourself,
including your full name, your major, and one or two
items that you most desire to learn in this class. Throughout this class, you
shall regularly participate at the discussion group to find recent
announcements, reminders, and discussions.
3.
Cyber
attacks: Explain what each of the following attacks
is. Cite your source(s).
Note: Not all information published on the web
are correct. Discern the validity of the information
you use by, for example, comparing them with what you have learned from
the textbooks and the class discussions.
a)
(10 pts) Replay
attacks b)
(10 pts) Man-in-the-middle
attacks c)
(10 pts) Explain the relationship
between replay attacks and Denial of Service (DoS) attacks. Hint:
How would the hacker use replay attacks
to cause Denial of Service? d)
(10
pts) Explain the differences between replay attacks and man-in-the-middle
attacks. Hint: They are different attacks. 4.
To prepare your computer for
the remaining hands-on labs, set up your computer according to instructions
given at this page: https://seedsecuritylabs.org/lab_env.html
a)
Download and install the virtual box first.
b) Next,
download the SEED Ubuntu16.04
VM image file to a folder in your computer.
c)
Unzip and copy the VM images to a folder.
d)
Configure the virtual box and
create a new virtual machine with the same name as your full name (e.g.,
JohnDoe as the name of the VM).
e)
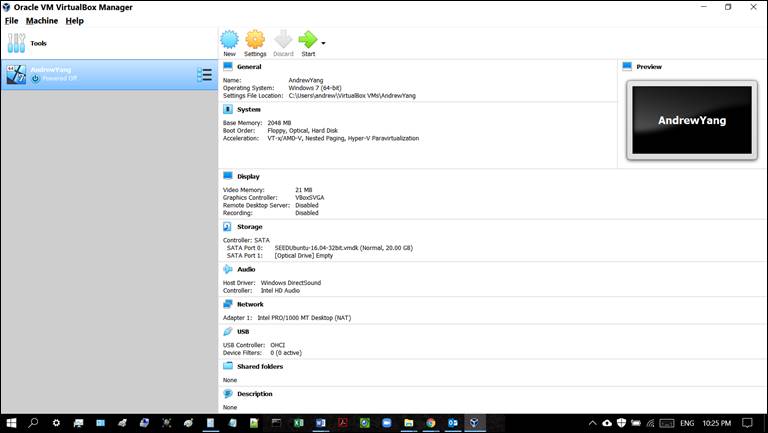
(10
pts) Print a screenshot of your VM created above (in
6.1.4). Note: Name the VM using your full name. Figure 1 shows a sample
screenshot.
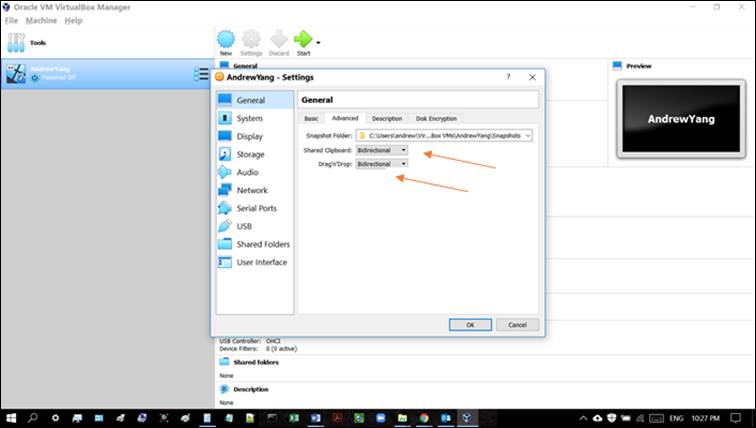
Note: As shown in Figure 2, in order to enable shared clipboard between the
VM and your computer’s OS, be sure to configure, in
Settings/General/Advanced, both ‘Shared Clipboard’ and
‘Drag’n’Drop’ to bidirectional.
5.
Answer the following questions:
a)
(10
pts) What is a virtual box? Hint: Explain its
relationship to the operating system. What is the role played by the virtual
box?
b)
(10
pts) What is the role played by the SEED Ubuntu16.04 VM image?
c)
(10
pts) How many VMs can you run simultaneously within a
virtual box?
d)
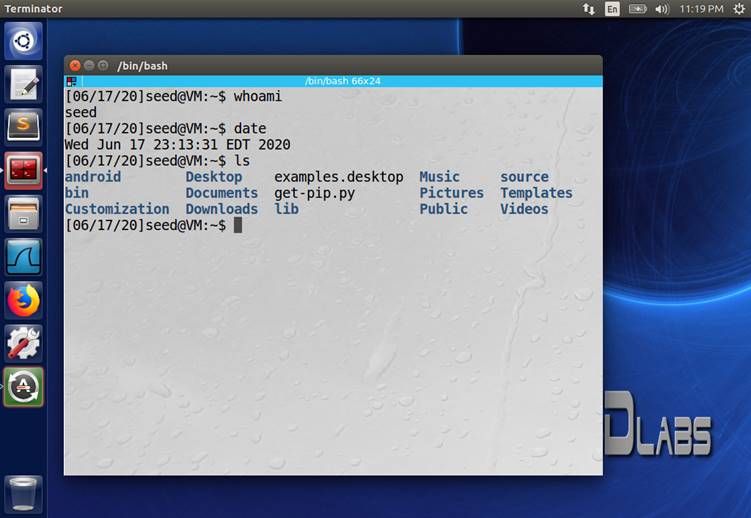
(10
pts) Start the VM created above in 6.1. Click the Terminator icon to activate a terminal
window within the VM. Enter the following three commands into the terminal
window: whoami, date, ls. Take a screenshot of the terminal window. See Figure 3 for an example
screenshot.
Go to the Index Total: 100
points 1. (5 pts) Decide whether you want to work on this lab by yourself
(i.e., a one-person lab team), or partner with another person in the class
(i.e., a two-person team). Indicate your team membership for this lab.
NOTE: This task is required of each person, whether he or she is in a
one-person or a two-person team.
2. Complete Tasks #1-#5 from the PKI lab (https://seedsecuritylabs.org/Labs_16.04/Crypto/Crypto_PKI/).
- Evaluation of the lab: You will earn 20% for having
successfully implemented each of the tasks. - Task #6 is a bonus (10% extra). - To hand in: a well-documented lab report including screen shots and explanations Go to the Index Total: 100
points 1. (5 pts) Decide whether you want to work on this lab by yourself
(i.e., a one-person lab team), or partner with another person in the class
(i.e., a two-person team). Indicate your team membership for this lab.
NOTE: This task is required of each person, whether he or she is in a one-person
or a two-person team.
2. Complete Tasks #1-#5 from the Buffer Overflow lab (https://seedsecuritylabs.org/Labs_16.04/Software/Buffer_Overflow/).
- Evaluation of the lab: You will earn 20% for having
successfully implemented each of the tasks. - Task #6 is a bonus (10% extra). - To hand in: a well-documented lab report including screen shots and explanations Go to the Index Research
Project & Presentations Note 1: This is an individual project. Note 2: Make sure you properly cite the work of
other researchers or professionals. Visit http://sce.uhcl.edu/yang/citing.htm
for more information about cited references. Warning: Missing or improper cited references in your abstract
and final report will result in poor score for your research project. The goal of this project is for you to visit refereed
publications (as well as some relevant web sites) to perform a detailed
investigation of a chosen research topic. The University Library has online
databases that could be used as a starting point of your literature search. The topic you choose should
be related to Cryptography and/or Software Security.
Do not select a broad topic such as Wi-Fi security or cloud security;
instead, choose a topic that is related to certain cryptographical
algorithm or a protocol/standard in Software Security. Visit https://en.wikipedia.org/wiki/List_of_cryptosystems
to view a list of cryptosystems. If you need suggestions when choosing the
topic, feel free to discuss it with the instructor. Items to be submitted:
A preliminary abstract of your presentation topic is due early
in the semester. Check the syllabus for the due date. Each student should
also present his/her abstract in class on the scheduled date. The
abstract should be 1-2 pages long (single-spaced), and contains the following
sections: (1)
Class
name (i.e., CSCI5233 Computer Security & Cryptography) (2)
Your
name and an email address that you check regularly (that is, at least once a
day) (3)
Topic
of your investigation (4)
General
description of the topic (5)
Why
have you chosen this topic, that is, its relationship to this course? (6)
Survey
of related work: Discuss at least three articles related to your
chosen topic. (7)
A
tentative outline (agenda) of your final report. That is, the
sections/subsections that you plan to include in the final paper.
1.
The
written report should be 5-10 pages long (single-spaced), and include your
findings about the chosen topic. 2.
The
following is a suggested outline of your final report:
i. Title
ii.
Your
name (and email address)
iii.
An
abstract (50-100 words)
iv.
Introduction
to the topic
v. Significance of the chosen topic with
respect to this course
vi.
Survey
of related work
vii.
Implemented
demonstrations, if applicable
viii.
Your
findings
ix.
Future
work: research ideas and projects related to the topic
x. Conclusion
xi.
Appendix
(if any) Go to the Index |
|
|||||||