|
T. Andrew Yang Email: yang@uhcl.edu Web: http://cse.uhcl.edu/yang/ Tel.: (281) 283-3835 |
Last updated: 8/7:
Enhanced Assignment 1 description 8/24/2021:
first posted |
|
||
|
CSCI 5234 Web Security
Note: Total points: 100 1.
(20 pts) Visit the class discussion group in the Blackboard. Post a message
with your full name as the subject line. In your post,
briefly introduce yourself, including your full name, your
major, and one or two items that you most desire to learn in this class. Throughout
this class, you shall regularly participate at the discussion group to find
recent announcements, reminders, and discussions. 2.
A refresher of Java Security: Download and install the
current version of Java Development Kit (JDK), and configure it to run the
Java Cryptography Extension (JCE) and the Bouncing Castle JCE Provider, by
following the instructions as specified in this page: https://sceweb.uhcl.edu/yang/teaching/JDK_JCE_environment_Configuration.htm.
NOTE: Adjust the version number in the instruction
file to reflect the current version of JDK. For example, if you have download
JDK 16, then all the version number in the instruction file ought to be
adjusted to 16. NOTE: To verify whether your configuration of the
JDK environment is correct or not, compile and run some of the sample
programs included in http://sce.uhcl.edu/yang/teaching/proJavaSecurityCode.html.
-
For example, BlowfishExample.java is
a sample program that does NOT require either unlimited strength
jurisdiction policy or the Bouncy Castle provider. You
may use it to test your initial JDK installation. -
FileEncryptor.java is
a program that can be used to test your JDK to determine whether it has the
proper Bouncy Castle provider configurations. -
KeysizeTest.java is
a program that can be used to test your JDK for unlimited strength
jurisdiction policy. Run the GenerateKeyPair.java
program to generate a key pair. NOTE: The Bouncing Castle Security Provider must be
added to the source program. See step #5 in the instruction file for detailed
statement to add the provider. NOTE: The generated private key will consist of two
separate files, one for storing the private key and the other for storing the
public key of that key pair. The private key will be used later by the Client
program to generate a digital signature; the public key, on the other hand,
will be used by the Server program to verify the signature in order to
authenticate the Client program. Study the source code
of the Client, SignatureAuthenticationClient.java, and
the source code of the Server, SignatureAuthenticationServer.java,
both of which are available at http://sce.uhcl.edu/yang/teaching/proJavaSecurityCode.html. NOTE: The Bouncing Castle Security Provider must be
added to the Client source program. See step #5 in the instruction file for
detailed statement about how to add the provider. 1)
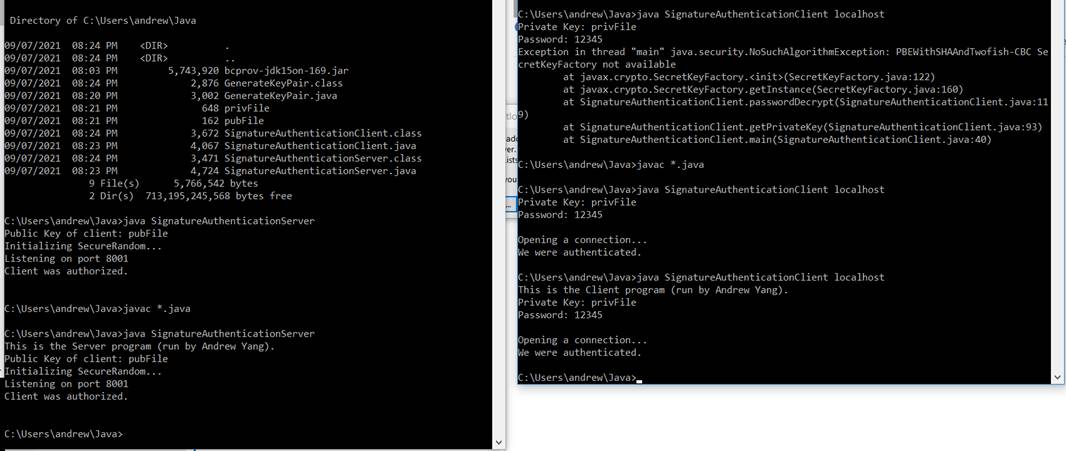
(40 pts) Run
the programs and hand in appropriate screen snapshots to show the execution
results. Add a statement to the beginning of the programs such that
the first output line shows your full name. Attach the screen output
as part of this assignment. Shown in Figure 1 is a sample output
of running those programs.
Figure
1. Sample screen output of running the Client and the Server programs 2)
(40 pts) When
receiving a digital signature from the client, how does the authentication
server verify the client's signature? That is, how would the
server know that the signature is really the client's? Go to the Index Total
points: 100 Study the textbooks
and/or applicable web sites to find answers for the following questions.
Online glossaries such as those listed in the syllabus page may also be used. Note: It
is required that you clearly identify the source(s) of your information.
Failing to cite the source(s) will cause reduction of points. 1) (10
pts) What is a ‘man-in-the-middle attack’? 2) (10
pts) What is a ‘replay attack’? 3) (10
pts) Is a replay attack a type of man-in-the-middle
attack? Justify your answer. 4) (10
pts) What is ‘pagejacking’? 5) (10
pts) What is a ‘session hijacking
attack’? 6) (10
pts) What is ‘web access management’? 7) (10
pts) What is ‘end-to-end security’? 8) (10
pts) Explain what 'input sanitization' is
and why it is critical for secure web operations. 9) (10
pts) What is ‘out-of-band
communication’? 10) (10
pts) What is 'two-factor authentication'? Why is
using more than one factor important in authenticating a user? Go to the Index Note: This
is an individual project. The goal of this project is for you to visit refereed
publications (as well as some relevant web sites) to perform a detailed
investigation of a chosen research topic. The University Library has online
databases that could be used as a starting point of your literature search. The topic you choose should be related to security of web-based
information systems. A
topic may be related to threats
against web-based information systems, attacks
that specifically target web-based systems, mitigations adopted for countering such threats and attacks, etc.
If you need suggestions when choosing the topic, feel free to discuss with
the instructor. Each person should
create and maintain a distinct discussion thread in the discussion group, by
posting to the discussion forum named 'Research projects should be posted
here". Progress of your project should be updated weekly in that
thread. How well you maintain your discussion thread is part of the grading. A benefit of this
approach is that both the instructor and your classmates will be able to view
your progress and, if applicable, share their thoughts and comments. Items to be submitted:
A preliminary abstract of your presentation topic is due early
in the semester. Check the syllabus for the due date. Each student should
publish his/her abstract in the class discussion board by the due
date. The
abstract should be 1-2 pages long, and contains the following sections: (1)
Class
name (i.e., CSCI5234 Web Security) (2)
Your
name and an email address that you check regularly (that is, at least once a
day) (3)
Topic
of your investigation (4)
General
description of the topic (5)
Why
is the topic related to web security? (6)
Survey
of related work Discuss at least three articles
related to your chosen topic. VERY
Important: Make sure
you properly cite the work of other researchers or professionals. Visit http://sce.uhcl.edu/yang/citing.htm
for more information about cited references. Warning:
Missing or improper
cited references in your abstract and final report will result in poor score
for your research project. (7)
A
tentative outline (agenda) of your final report. That is, the
sections/subsections that you plan to include in the final paper.
1.
The
written report should include your findings about the chosen topic. 2.
A
draft of the final report should be published in the class discussion
group to solicit comments from your classmates and the instructor. Warning: Missing or improper cited references in
your abstract and final report will result in zero or poor score for this
assignment. 3.
The
following is a suggested outline of your final report:
i. Title
ii.
Your
name (and email address)
iii.
An
abstract (50-100 words)
iv.
Introduction
to the topic
v. Significance of the chosen topic with
respect to the security of web-based applications
vi.
Survey
of related work
vii.
Implemented
demonstrations, if applicable.
viii.
Your
findings
ix.
Future
work: research ideas and projects possibly related to the topic
x. Conclusion
xi.
Appendix
(if any) Go to the Index Note about hands-on labs: Note:
The lab may be completed by an individual person or by a team of
two persons. A team can consist no more than two persons. -
You are welcome to use your own laptops to implement the hands-on labs
(by setting up virtual boxes and virtual hosts on it). -
For those who prefer to use university computers, some of the computers
in the D201 lab are reserved for this class. -
To get access to the D201 lab, contact the Computer Science secretary
to set up access privileges. Preparation
for the hands-on labs: Go over the following documents before starting
your hands-on labs. Lab 1 Cross Site Request Forgery (CSRF) Total: 100
points Complete the CSRF lab from the SEED project.
Description of the
lab, additional information, and other resources about the lab can be found
on the SEED project website; see https://seedsecuritylabs.org/Labs_16.04/Web/. NOTE: For this lab, follow the instructions as given in the Description page
from https://seedsecuritylabs.org/Labs_16.04/Web/Web_CSRF_Elgg/. A local copy of the Description can be found here.
In addition, more
information about the specific lab can be found in the textbook by Dr. Du.
Check out these supplementary
notes about implementing this lab.
-
Evaluation of the
lab:
A. (60%) You will earn 15% for each of the tasks successfully implemented and
demonstrated to the TA.
B. (40%) Hand in a detailed lab report to describe what you have done and what
you have observed. Please provide details using Firefox’s add-on tools,
Wireshark, and/or screenshots. You also need to provide explanation to the
observations that are interesting or surprising.
Go to the Index Lab 2 Cross-site Scripting (CSS) Total: 100
points Complete the CSS lab from the SEED project.
Description of the lab,
additional information, and other resources about the lab can be found on the
SEED project website; see https://seedsecuritylabs.org/Labs_16.04/Web/. NOTE: For this lab, follow the instructions as given in the Description page
from https://seedsecuritylabs.org/Labs_16.04/Web/Web_XSS_Elgg/. A local copy of the Description can be found here.
In addition, more
information about the specific lab can be found in the textbook by Dr. Du.
Check out these supplementary notes
about implementing this lab.
-
Evaluation of the
lab:
C. (70%) You will earn 10% for each of the tasks successfully implemented and
demonstrated to the TA.
D. (30%) Hand in a detailed lab report to describe what you have done and what
you have observed. Please provide details using Firefox’s add-on tools,
Wireshark, and/or screenshots. You also need to provide explanation to the
observations that are interesting or surprising.
Go to the Index Lab 3 SQL Injection Total: 100
points Complete the SQL Injection lab from the SEED
project.
Description of the
lab, additional information, and other resources about the lab can be found
on the SEED project website; see https://seedsecuritylabs.org/Labs_16.04/Web/. NOTE: For this lab, follow the instructions as given in the Description page
from https://seedsecuritylabs.org/Labs_16.04/Web/Web_SQL_Injection/. A local copy of the Description can be found here.
In addition, more
information about the specific lab can be found in the textbook by Dr. Du.
Check out these supplementary
notes about implementing this lab.
-
Evaluation of the
lab:
E. (80%) You will earn 10% for each of the tasks/sub-tasks successfully
implemented and demonstrated to the TA.
F. (20%) Hand in a detailed lab report to describe what you have done and what
you have observed. Please provide details using Firefox’s add-on tools,
Wireshark, and/or screenshots. You also need to provide explanation to the
observations that are interesting or surprising.
Go to the Index |
|
|||