|
T. Andrew Yang
|
Last updated: 03/25/2025: Lab 2 posted 02/06/2025: Lab 1 posted |
||||||
CSCI
3341 Cyber Attacks and Defense
Total: 100 points
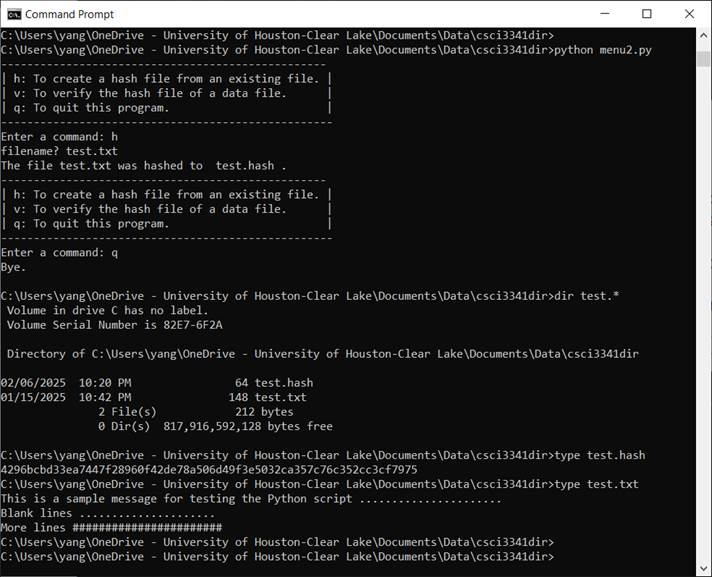
1. In the in-class assignment #3 (Creating
a hash file), you developed a program that reads data bytes from a file,
generates a hash value from those bytes, and then saves the hash value into a
.hash file. In this exercise, you will complete the 2nd
half of the process by extending the program you developed for in-class EX#3 to
do the following:
1.1. (25
pts) In
the main function, add a simple user menu (as shown below) to take user’s
input.
>
Enter a command (h, v or q):
h: To
create a hash file from an existing file.
v: To verify
the hash file of a data file (for example, text1.hash and text1.txt) and report
whether the data file can be trusted or not.
q: To
quit this program
Figure 1 is a sample
screen output shows how the menu may look like.
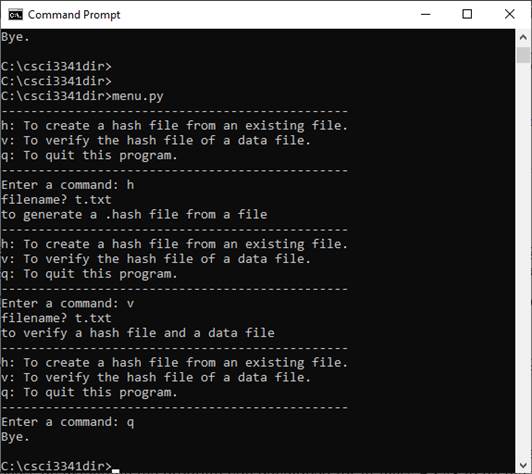
Figure 1: A sample menu
for user interface
To hand in:
a.
The source code
b.
A screenshot of running the program
1.2. (25
pts)
(Continued from the above) Implement the function when the user enters ‘h’.
Hint: This is the program that you developed for EX2 in the in-class assignment
#3.
As shown in Figure 2, when the user enters ‘h’,
the program asks for the name of the file to be hashed.
It then hashes the content of that file and saves the hash value into a .hash
file.
Figure 2: A sample
screenshot of running the ‘h’ option
To hand in:
a.
The source code
b.
A screenshot of running the program
1.3. (25
pts)
(Continued from the above) Implement the function when the user enters ‘v’.
The program first asks for the name of the file
to be verified (for data integrity). Suppose the user
enters a.dat as the file name. The program will try to open the hash file
a.hash. If it does not exists, it will display an error message indicating that
the hash file does not exist; otherwise, the program hash the content of the
data file (say, a.dat) and then compares the hash value with the content of the
hash file (say, a.hash). If the two hashes are the same, it reports that the
data file is correct; otherwise, it reports that the data file cannot be
trusted.
To hand in:
a.
The source code
b.
A screenshot of running the program
1.4.
(25 pts) In a Man-in-the-Middle attack, the attacker changes the data and generates a new hash
value out of the modified data. The attacker then uses the modified data and
its hash value to replace the original data and hash value. When the user tries
to validate the integrity of the data file, he/she/it will determine that the
content of that data file is correct. Therefore, a successful man-in-the-middle
attack will defeat the ‘data integrity’ service, which is supposed to be provided by using hashing.
In this exercise, simulate a man-in-the-middle
attack by creating a program that opens and reads an existing data file,
modifies its content, generates the new hash value, and then uses the new hash
value to overwrite the original hash file.
To hand in:
a.
The source code
b.
A screenshot of running the program
Go to
the Index
Total:
100 points
In Task
#2 of the in-class assignment #6 (https://uhcl.instructure.com/courses/16380/assignments/337722),
you developed two programs, BobSign2.py and AliceVerify2.py. The tasks in this
lab are based on those two programs.
2.1 (30
pts) In
the exercise, add Sockets Communication to the two programs. The revised
programs, BobSign3.py and AliceVerify3.py, will communicate over sockets. Data
to be sent from Bob to Alice include the original
message and the signature generated by Bob out of that message. Before Alice
verifies the received message and signature, make sure
Alice has access to Bob’s public key. The result of signature verification should be sent back to Bob as a confirmation. Bob will
display the received confirmation on its screen.
To hand in:
a.
The source programs
b.
Screenshots of running the programs
2.2 (20
pts) Run
the two programs you developed from the above exercise, BobSign3.py and
AliceVerify3.py, on two different computers over a local area network (LAN).
Revise the programs such that the screen outputs will show each computer’s IP
address and the port number used by the respective program.
To hand in:
c.
The revised source programs
d.
Screenshots of running the programs over a LAN
2.3 (50
pts) Add
confidentiality to the above two programs. In the revised programs,
BobSign4.py and AliceVerify4.py, Bob will encrypt the message using AES with
a 256-bit key (in CBC mode) and send the ciphertext and the signature to
Alice. Alice, upon receiving the ciphertext and the signature, will use the pre-shared
AES key to decrypt the ciphertext. The decrypted data will then be used for the purpose of verifying the signature. Run the revised
programs on two different computers over a local area network. In the screen
outputs, show each computer’s IP address and the port number used by the
respective program.
To hand in:
e.
The revised source programs
f.
Screenshots of running the programs over a LAN
Go to
the Index